|
clownstrike is more of a joke on the name than the company
|
|
|
|

|
| # ? Jun 7, 2024 21:18 |
|
as far as EDR vendors and "threat intel" companies go, they're one of the better ones I think
|
|
|
|
cool cool. the job does sound kind of neat and I imagine it would be a big pay bump, but I've had enough of silicon valley for a while. the 9 hour time difference is rough good to know that the clownstrike name isn't too serious in case I ever need... whatever they do
|
|
|
|
the only time i hear about crowdstrike good or bad is when the mac users at work are complaining about it eating all their CPU on the linux side it seems to have calmed down a bit since they switched from their old C++ kernel module to their new eBPF sensor backend i don't really know if our IT/security department does anything useful with it or if it's just another component in the security compliance checkbox industrial complex
|
|
|
|
Crowdstrike has a new-ish thing that tries to identify sites "associated" with your company. So in our case it looked at our home page, saw a link to microsoft.com and decided anything with a certificate issued to a subdomain of Microsoft is our problem. So some dweeb in infosec pages me about some random IP with RDP exposed to the Internet with a certificate matching microsoft.com. The team doesn't even know what this thing does so they want me to mark each finding as a FP instead of a fundamental fix. Their integration with AWS blows too. Infosec will give me a report of some instances ip-10-whatever.ec2.internal that have some out of date version of curl or whatever. But no tags, so I have no idea what it is. Whatever had that IP 3 days ago is long gone and if there's something using it now it's not the same. Sure I can probably find in cloudtrail something about it, but I have no aggregate view of where my problems are so I can't prioritize issues. I don't have a problem with the findings, excepting the RDP crap. I just have a hard time making use of it. It makes some pretty dashboards, but it doesn't help my team fix anything more efficiently.
|
|
|
|
I've liked Crowdstrike, it's been helpful any time we need to call the feds 
|
|
|
|
Clownstrike ate my cpu, then it ate binaries that I compiled. But in the end I think the problem is how it’s used. The dipshit ITSEC ppl at my job have turned of any client side notifications to “avoid tipping of the bad guys” which meant I was extremely frustrated when .exe files I created just went poof… I only figured it out because the same thing happened to a colleague earlier, then they contacted him 2 weeks after the thing happened. I much prefer it to TLS inspection, and I don’t see how it can run on developer machines without causing more trouble than anything good
|
|
|
|
zokie posted:Clownstrike ate my cpu, then it ate binaries that I compiled. But in the end I think the problem is how it’s used. The dipshit ITSEC ppl at my job have turned of any client side notifications to “avoid tipping of the bad guys” which meant I was extremely frustrated when .exe files I created just went poof… I only figured it out because the same thing happened to a colleague earlier, then they contacted him 2 weeks after the thing happened. crowdstrike super hates devs. ive seen this exact scenario multiple times. hopefully your security team put dev computers in a different group from all the other user computers and tune the policies better.
|
|
|
|
zokie posted:Clownstrike ate my cpu, then it ate binaries that I compiled. But in the end I think the problem is how it’s used. The dipshit ITSEC ppl at my job have turned of any client side notifications to “avoid tipping of the bad guys” which meant I was extremely frustrated when .exe files I created just went poof… I only figured it out because the same thing happened to a colleague earlier, then they contacted him 2 weeks after the thing happened. tell me nobody in itsec has ever tried their hand at fighting EDR without telling me ..... yeah sorry dude, that sucks. FungiCap posted:crowdstrike super hates devs. ive seen this exact scenario multiple times. hopefully your security team put dev computers in a different group from all the other user computers and tune the policies better. it can be done but you need more knowledgeable dudes at the helm, preferably working with your devops plumbers. I feel your pain.
|
|
|
|
we've had 2-3 SOC analysts leave to work at Crowdstrike, they offer good money and have roles where you can do actually cool stuff. they seem to always be aggressively hiring, mainly targeting people with 2-3 years experience working in a SOC. haven't heard any complaints from those who left to work there. Crowdstrike Falcon EDR/XDR is a fairly good product when configured appropriately. the exploit mitigation/attack surface reduction stuff is optional and can be fine-tuned. you can assign assets to groups and then apply different policies based on those groups which helps you to secure the critical stuff and stop devs from complaining. even with the mitigation stuff disabled it's worth having just as a sensor for IoC detection. this goes well with the threat hunting tools they've got. one anecdote i've heard about Crowdstrike but not really sure if it's true: years ago when they were in full start-up mode they rushed the architecture design to stand-up the first instance of their SaaS platform, US-1. this lead to some fairly severe issues when they tried to scale it out so they said "gently caress it" and started from scratch with a new architecture which was stood-up as US-2. from a customer's perspective they both function identically however they have different API versions and endpoints, even to login (US-1), US-2)). if your CID is on US-1 you can raise a ticket to migrate to US-2 however it's very disruptive. so they just keep them both running lol oh also all their SaaS instances (US-1, US-2, US-GOV-1 and EU-1) are running on AWS: https://aws.amazon.com/solutions/case-studies/crowdstrike/. apparently their bill is monstrous, like 9-figgies
|
|
|
|
Got 2 critical cases from a customer who somehow deployed all their personal passwords to all their users' Chrome/Chredge profiles.
|
|
|
|
rip lol, that’ll be fun to sort out if any of the users have logins to the same sites
|
|
|
|
depending on how "personal" the logins are there's potentially no ceiling to the amusement.
|
|
|
|
FungiCap posted:crowdstrike super hates devs. ive seen this exact scenario multiple times. hopefully your security team put dev computers in a different group from all the other user computers and tune the policies better. we have it on our dev machines and it seems fine. the only time I've been pinged by IT is because i ran a sketchy looking allen & heath firmware updater needed an intel cpu to run on, which seemed fair.
|
|
|
|
Achmed Jones posted:For what it's worth, I have a hard time thinking of _any_ organization where I say "OMG they work at _____." I guess maybe, like, NSA crypto, but even then, it depends a ton on what the actual job is and the things that come out of their mouth when we speak and such. i think it's impressive that my college friend works (partially) at NIST but he also has a physics PhD relevant to quantum computing
|
|
|
|
zokie posted:Clownstrike ate my cpu, then it ate binaries that I compiled. But in the end I think the problem is how it’s used. The dipshit ITSEC ppl at my job have turned of any client side notifications to “avoid tipping of the bad guys” which meant I was extremely frustrated when .exe files I created just went poof… I only figured it out because the same thing happened to a colleague earlier, then they contacted him 2 weeks after the thing happened. We haven't had those issues. I helped make sure that devs are in a policy group separate from general users though. And we get alerts that are acted on by either us or Crowstrike's support within a few minutes. Someone probably has to do some configuration work. I haven't noticed their sensor using significant resources on Windows or Linux machines. Haven't tried it on Macs.
|
|
|
|
Just a quick question. What is the go to for a password manager for a team? We currently have a Keepass DB on a shared drive but obviously lacks important features like audit trails, different accounts for access etc. What is everyone else using in this space?
|
|
|
|
we're using bitwarden internally, and for a few of our clients. we're using the hosted option, so it's a paid service, but it works well.
|
|
|
|
infernal machines posted:we're using bitwarden internally, and for a few of our clients. we're using the hosted option, so it's a paid service, but it works well. our team maintains Vault for general purpose secret storage across the org, which extends to both user secrets and app secrets. user auth is tied into Okta and app auth uses the kubernetes auth backend. the Vault GUI is now included in the free license so anyone can use it without having to learn CLI tooling. a vault cluster may be more than you want to maintain just for shared secret storage but it's honestly pretty good for a Hashicorp product
|
|
|
|
Varkk posted:Just a quick question. What is the go to for a password manager for a team? We currently have a Keepass DB on a shared drive but obviously lacks important features like audit trails, different accounts for access etc. What is everyone else using in this space? we use 1pass, it seems to work well ¯\_(ツ)_/¯ I haven't dug too far into the security implications because IT owns it and not the security team
|
|
|
|
Varkk posted:Just a quick question. What is the go to for a password manager for a team? We currently have a Keepass DB on a shared drive but obviously lacks important features like audit trails, different accounts for access etc. What is everyone else using in this space? we're using azure keyvault, and while it works great for automation and app secrets it is poo poo for user secrets if it was my decision would just use 1pass or bitwarden for team/user secrets
|
|
|
|
Varkk posted:Just a quick question. What is the go to for a password manager for a team? We currently have a Keepass DB on a shared drive but obviously lacks important features like audit trails, different accounts for access etc. What is everyone else using in this space? https://www.keepersecurity.com
|
|
|
|
i like the password inspector on the front page
|
|
|
|
related to the password chat: anyone got a good suggestion for a secure api key storage? my company has keeper but apparently everyone with access can see everything so I’m looking for alternatives I can host myself. we’re too poor for Amazon secrets apparently.
|
|
|
|
just lmao that aws secrets bills per secret and per api call azure keyvault at least is only transaction billing just use vault though
|
|
|
|
susan b buffering posted:we have it on our dev machines and it seems fine. the only time I've been pinged by IT is because i ran a sketchy looking allen & heath firmware updater needed an intel cpu to run on, which seemed fair. I don't even know what we use here but I'll never forget the day I was emailed for quote:cat .bash_history|grep ssh|uniq -u Like I loving get it but that's creepy as hell and I don't even have ssh keys set up so the biggest concern isn't even a concern. stoopidmunkey posted:related to the password chat: anyone got a good suggestion for a secure api key storage? my company has keeper but apparently everyone with access can see everything so I’m looking for alternatives I can host myself. we’re too poor for Amazon secrets apparently. Show your boss you think like a manager: Use the excel API to store everything in an encrypted spreadsheet. Internet Old One fucked around with this message at 17:27 on Mar 15, 2024 |
|
|
|
we use keeper and I like it. I did most of the initial setup and implementation for us, including deploying the automator login service container in Azure. We just passed one year of using Keeper actually, I renewed the cert this week.
|
|
|
|
stoopidmunkey posted:related to the password chat: anyone got a good suggestion for a secure api key storage? my company has keeper but apparently everyone with access can see everything so I’m looking for alternatives I can host myself. we’re too poor for Amazon secrets apparently. just put export AWS_SECRET in .bashrc
|
|
|
|
Internet Old One posted:I don't even know what we use here but I'll never forget the day I was emailed for I bet they have a trigger on “history” because deleting history is a common attacker move also, gotta point out the gratuitous 🐱
|
|
|
|
Internet Old One posted:cat .bash_history|grep ssh|uniq -u btw you can ctrl-r and then type part of a command and keep hitting ctrl-r to get previous incantations also i just installed https://atuin.sh on my work computer to try it out, seems to work pretty well (gives you a big ol display when you search history so its easier to find the correct one, but disable the up arrow imo)
|
|
|
|
Related, in powershell I run a thing called PS-ReadLine which does a predictive preview of commands from your history: https://devblogs.microsoft.com/powershell/announcing-psreadline-2-1-with-predictive-intellisense/?WT.mc_id=-blog-scottha 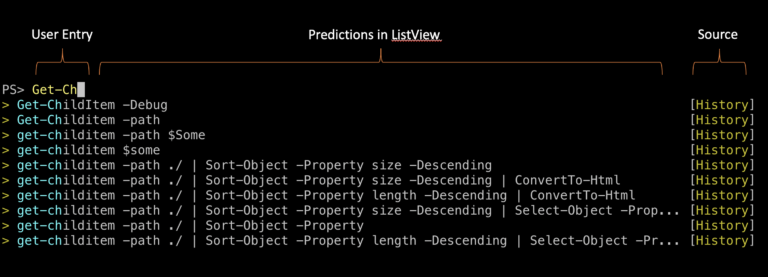 Is there anything like this for bash?
|
|
|
|
The Fool posted:Related, in powershell I run a thing called PS-ReadLine which does a predictive preview of commands from your history:
|
|
|
|
ctrl-r behaves considerably differently
|
|
|
|
Subjunctive posted:I bet they have a trigger on “history” because deleting history is a common attacker move hope they have a trigger on unset HISTFILE too
|
|
|
|
ya vanilla bash ctrl-r is just jumping to previous with substring, but the atuin thing seems similar to that powershell thing
|
|
|
|
if yall dont set up fzf with ctrl-r instead of the bash/zsh built-in i dont even know what to tell you The Fool, you probably want fzf
|
|
|
|
been using atuin, will probably try fzf at some point
|
|
|
|
yeah fzf is real good
|
|
|
|
Subjunctive posted:I bet they have a trigger on “history” because deleting history is a common attacker move Good catch! I do it intentionally because my brain wants to search a file for a thing in that order and so I have a bad habit of entering the parameters backward. It's not just about covering tracks. If you compromise an account there is a good chance you can access other accounts they have with their ssh keys or their password if you know it. Internet Old One fucked around with this message at 22:30 on Mar 15, 2024 |
|
|
|

|
| # ? Jun 7, 2024 21:18 |
|
Achmed Jones posted:if yall dont set up fzf with ctrl-r instead of the bash/zsh built-in i dont even know what to tell you yeah, that's exactly what I was looking for thanks
|
|
|
















































