|
Last Chance posted:i remember i tried this with a key i got through some MS win 7 upgrade promotion and it would only let me download a french or korean windows 7 iso lol the windows 10 download page can be coerced into showing download options for windows 7 and 8 as well with a little js
|
|
|
|

|
| # ¿ May 5, 2024 09:30 |
|
Munkeymon posted:you could just make the user interact with each field individually but the list is still better UX as has been said many times before, security often comes at the expense of convenience. solution: patch autofill out of all of these browsers
|
|
|
|
secfuck thread: the most secure thread on the forums for 24 short hours
|
|
|
|
Keep up the good work hackbunny, these posts are awesome RE: disk size I checked with the current version of vmware workstation, and if you provision an XP machine without changing any of the default settings you get a 45GB disk (and one cpu and 512mb of ram lol)
|
|
|
|
Rufus Ping posted:assuming you arent joking, please explain reduction (arguably elimination) of attack surface If your password manager is filling out forms for you, it's probably doing some outrageous poo poo like injecting JS into the page you're viewing. Bridging the browser / password manager gap is how we ended up with multiple lastpass vulns along the lines of "whoops, turns out we exposed all your passwords to any website that asked for them"
|
|
|
|
I'm the censorship of the word "chinese"
|
|
|
|
flakeloaf posted:the dot product of an attack vector
|
|
|
|
some bored college student hijacked his own campus' IoT devices and used them for a DDOS against said uni's DNS servers http://www.zdnet.com/article/how-iot-hackers-turned-a-universitys-network-against-itself/ quote:
Default credentials, as always
|
|
|
|
LeftistMuslimObama posted:do any of you know much about Carbon Black? it's apparently an application whitelisting program for windows that they're rolling out here at work. i'm just curious how many ways it inadvertently links other user activity to the admins or vendor, as it sounds like the vendor has to actually help our local admins add things to the whitelist from the internal memo. man I had this idea years ago. Wrote a service that acted as a whitelist for other windows services. Listened for service start events and killed any service that attempted to start but wasn't allowed by the whitelist my goal was to stop IT from pushing software onto my work machine via the domain / group policy, lol it didn't end well
|
|
|
|
Midjack posted:should we just call environmental detection and subsequent behavior modification "vdubbing" from now on? I like this idea
|
|
|
|
sha1 is dead long live sha1
|
|
|
|
E: wrong thread lol
burning swine fucked around with this message at 22:44 on Feb 27, 2017 |
|
|
|
OSI bean dip posted:when is nilbog going to be done? a week, two tops
|
|
|
|
Volmarias posted:To play devil's advocate, this is only the numbers for devices that still contact the play store (iirc). All the garbage Chinese spin-offs that don't come with Google preloaded, or where the user isn't signed into a Google account (I ran into someone with a G1 a couple years back who never signed into a Google account on the device, and didn't realize that there was an app ecosystem) won't be counted in these numbers. I tried about a year ago to do android sans google, and it's a loving mess. Even if you install apps from alternate stores (f-droid, etc), drat near everything expects the play framework to be present and will just crash when the api calls fail. Android without google these days basically means android without apps, I doubt there are really that many people in that segment
|
|
|
|
hobbesmaster posted:there's an alarming number of embedded devices doing this though oh yeah, I guess there are. welp
|
|
|
|
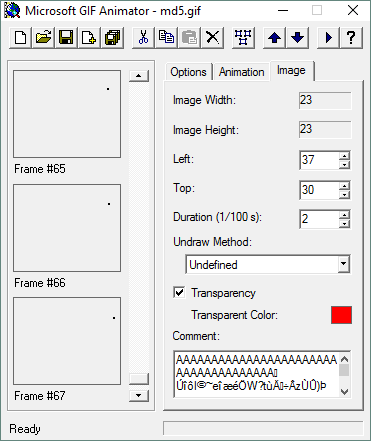
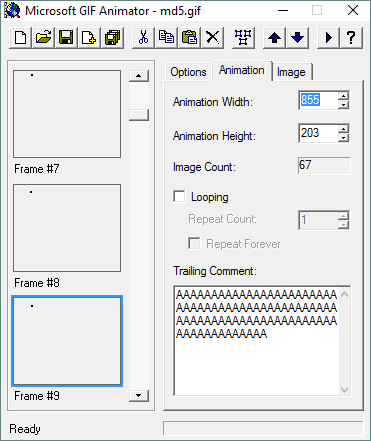
fishmech posted:that's actually a 67 frame animated gif that applies changes per each frame that are visually invisible (and which doesn't loop, probably chosen that way because it changes the contents slightly to do it). they also use the per-frame comment feature and the trailing comment feature to further massage the stored data in the file to get the preferred md5 i'm microsoft gif animator '95 running in windows 10
|
|
|
|
anthonypants posted:did anyone post this one yesterday http://www.zdnet.com/article/leaked-us-military-files-exposed/ this would be big news except the OPM already leaked all of this poo poo and more like 3 years ago e: although i guess that data didn't end up publically on the internet so welp
|
|
|
|
alternate headline: Chinese government better at protecting US secrets than US air force
|
|
|
|
Truga posted:wait, synergy costs money now? I was pretty annoyed by this, they started charging right at the same time that they completely broke synergy on linux. They broke their poo poo then began charging to update to a working version arch even created a package with this description: code:
|
|
|
|
infernal machines posted:er... bitlocker? annual reminder that bitlocker was significantly weakened after windows 7 with the removal of the diffuser 
|
|
|
|
Raere posted:I don't understand why password managers are so bad. Shouldn't they be relatively straightforward to make with some competent security people on your team? I understand that antivirus software is pretty complex so there are secfucks abound, but password managers shouldn't be that complex. the problems are almost always related to browser integration. keepass doesn't have browser integration, and as far as I'm aware, their only fuckup thus far was checking for updates over http (which was fixed after some whining by the author) e: 1pass has a pretty clean record so far as well, right? lastpass is the only one getting flagged for stupid poo poo like this on a weekly basis burning swine fucked around with this message at 21:21 on Mar 21, 2017 |
|
|
|
OSI bean dip posted:https://www.reddit.com/r/programming/comments/60jc69/company_with_an_httpserved_login_form_filed_a/df7vnzp/ also: quote:Unsurprisingly passwords are stored in plain text and trivial to get out of the database due to verbose logging.
|
|
|
|
l o l https://www.helpnetsecurity.com/2017/03/21/nest-security-cameras-stop-recording/ quote:Google Nestís Dropcam, Dropcam Pro, Nest Cam Outdoor and Nest Cam Indoor security cameras can be easily disabled by an attacker thatís in their Bluetooth range, a security researcher has found. Reported to Google: October 26, 2016 Public Disclosure: March 17, 2017 https://github.com/jasondoyle/Google-Nest-Cam-Bug-Disclosures/blob/master/README.md
|
|
|
|
BillWh0re posted:2017 and this linux user still can't get sound in his browser
|
|
|
|
OSI bean dip posted:this is an e-mail a colleague got Dear Mr. REDACTED NAME: Attached is an email that I received on March 24, 2017. I feel that you should be aware that some rear end in a top hat is signing your name to stupid spam emails. Very truly yours, OSI bean dip
|
|
|
|
lol just checked and my personal site's cert is signed by geotrust time to dehumanize i guess
|
|
|
|
schranz kafka posted:ive been talking about this and the main reaction ive been getting is "why? they're going to fix the holes" but i still feel like i should move to 1password Tavis has descended from the heavens and fixed all of their stupid problems, but once he's done he will move on and the lastpass team will continue to introduce new fuckups
|
|
|
|
Looks like they turned on basic http auth not posting the tweet because the IP is right there in screenshot
|
|
|
|
why have i never thought of this
|
|
|
|
lol I was going to suggest putting it in the thread title but I didn't want to post the actual string lest radium's vengeful spirit come to harvest our souls
|
|
|
|
WinNuke: now for linux edit: dammit this probably impacts my retard phone
|
|
|
|
ate all the Oreos posted:i just overheard our sysadmin talking about how much he loves getting targeted advertising because it's helpful and he's okay with them harvesting all his data because "it's anonymous" lol forever at people who think like this most that I know work for advertising companies and rationalize their own line of work like this so they can pretend that what they do isn't profoundly unethical see also: people working for "relevant marketing" companies and insisting that what they do isn't advertising at all
|
|
|
|
reuse your bits but also EMILY BLUNTS posted:if only the convention centre put the doors in a nonstandard location 
|
|
|
|
ate all the Oreos posted:im the guy in the comments trying to sell their own weird email service and whining that people don't trust it even though he charges money. y-combinator proceeds to get really happy about the "value proposition" and other capitalism things, yet not a single visiter with a y-combinator referrer signs up The headlines on this one have been amusing this morning quote:Unroll.me head 'heartbroken' that users found out it sells their inbox data We're sorry. So sorry. So sorry that you caught us
|
|
|
|
hey if I ever wanted to hide my_crimes.txt i'd just throw it smack in the middle of a long eula
|
|
|
|
I'm with you here though, shaggs. Anyone who gives a third party service their email login credentials deserves whatever happens to them and then some
|
|
|
|
infernal machines posted:mainframe of theseus NICE! Number19 posted:have some more atlassian fuckups while we're at it: https://confluence.atlassian.com/doc/confluence-security-advisory-2017-04-19-887071137.html lol atlassian My company switched to hipchat a while ago, and I noticed that whenever someone sends a picture (which is frequently a screenshot of something proprietary, or at least not meant for disclosure), it ends up hosted on an s3 instance with absolutely no authentication. URL is something like s3.amazonaws.com/uploads.hipchat.com/[comany's unique ID]/[some other id]/[upload.png] I'd been meaning to do some prodding and see if [some other id] is predictable, maybe I should take that off the back burner
|
|
|
|
Subjunctive posted:just stick a UUID in there and it's basically as good as authentication over https. It's waaaaaay too short to be a UUID e: just compiled a list of all the urls sent to me. It's more or less on par with an imgur identifier. Meh, not as interesting as I had hoped burning swine fucked around with this message at 19:07 on Apr 26, 2017 |
|
|
|
Good writeup on the security dumpster fire that is SugarCRM: http://karmainsecurity.com/tales-of-sugarcrm-security-horrors
|
|
|
|

|
| # ¿ May 5, 2024 09:30 |
|

|
|
|